Software Vendors
The Trusted Computing Group (TCG) assembled a list of software vendors supporting the TCG Opal specification in 2011. The full document is available from TCG here.
For Windows 8 and 10, Pro and Enterprise editions, Microsoft Bitlocker works without any further software installation. Also for client use on virtually any Windows or Linux platform that supports a hard disk password, a TCG Opal drive, if not converted to Bitlocker or native Opal mode by other other software, can be set up and locked in preboot using the settings preboot already provided for the computer. So, this method too involves no additional software.
However, if IT needs to manage the SEDs in its environment, or if there is a desire for Cloud Management, there are many commercial products.
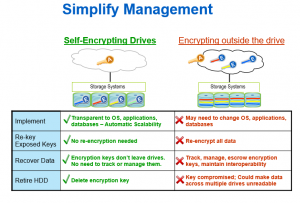
Keep in mind that hardware-based self-encryption is superior to software-based encryption for at least the following reasons:
- Transparency: SEDs come from factory with the encryption key already generated by a random number generator on board and never externalized.
- Ease of management: No encrypting key to manage; you do manage the authentication key.
- Life-cycle costs: The cost of an SED is pro-rated into the initial drive cost;
software has continuing life cycle costs. Current generations of SEDs have no price differential. In fact, most SED vendors have ALL drive being SEDs. - Disposal or re-purposing cost: With an SED, erase on-board encryption key (Crypto-Erase) and the drive is instantly erased; the encrypted data is not readable. No lengthy and error-prone over-writing is needed.
- Re-encryption: With an SED, there is no need to ever re-encrypt the data.
- Performance: No degradation in SED performance. Each SED has its own independently operating encryption engine.
- Standardization: The whole drive industry is building to the TCG/SED Specifications, which provide a common interface for managing multi-vendor SEDs. Keep in mind that the Drive Trust Alliance provides open-source client management code for a number of operating systems.
- Isolation: No interference with upstream processes, like Data Loss Prevention, De-duplication, and Data Compression, since the encryption occurs inside the drive.
The encryption for SEDs is built in hardware directly in the drive electronics, transparently; where data-at-rest encryption should be. In EVERY study, SEDs beat software-based encryption in every measure: transparency, ease of use, performance, cost, management, etc. Crypto-Erase is only reliable with SEDs, not software encryption: simply delete the on-board encryption key and the drive is instantly erased = encrypted data is unreadable. SED-based crypto-erase is officially recognized in the “bible” for drive sanitization: NIST SP800-88R1.