Are SEDs Secure?
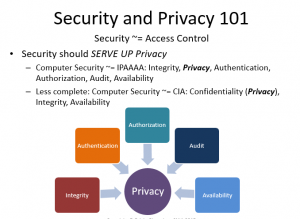
Computer Security is all about preventing your information assets from being controlled by others. It is all about access control.
Computer Security technology is highly mature but is all too frequently imperfectly implemented.
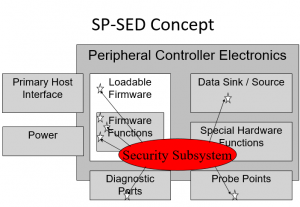
One of the best ways to analyse computer security is through an attack surface analysis. The TCG Opal drives that are FIPS 140-2 Certified pay attention to a security subsystem that controls access to all the major attack surfaces on a SED.
But the software (and hardware) that is external to the SED also pr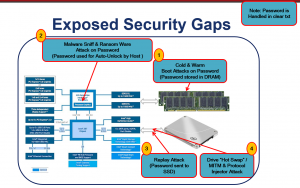 esents an attack surface, and this one can be much larger and more complicated than the SED’s attack surface. If, for example, the authentication KEK is typed in when the OS is active, the entire OS provides an attack surface which is, for all practical purposes, impossible to characterize. This is why we generally prefer pre-OS Boot unlocking (and setup) of SEDs. The pre-OS Boot environment provides a much smaller software attack surface. It is still very large and is very difficult to enumerate (since it can encompass boot code and what is called option ROM code — code in graphics cards on the mother board, network cards, etc.)
esents an attack surface, and this one can be much larger and more complicated than the SED’s attack surface. If, for example, the authentication KEK is typed in when the OS is active, the entire OS provides an attack surface which is, for all practical purposes, impossible to characterize. This is why we generally prefer pre-OS Boot unlocking (and setup) of SEDs. The pre-OS Boot environment provides a much smaller software attack surface. It is still very large and is very difficult to enumerate (since it can encompass boot code and what is called option ROM code — code in graphics cards on the mother board, network cards, etc.)
TCG is currently working on closing the att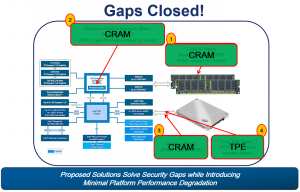 ack surfaces on TCG SEDs. One method, CRAM, separates authentication from the from the KEK, using public key cryptography. The second TPE will block even hot-swap attacks after a drive is unlocked.
ack surfaces on TCG SEDs. One method, CRAM, separates authentication from the from the KEK, using public key cryptography. The second TPE will block even hot-swap attacks after a drive is unlocked.
Generally speaking, attack is always possible. Mortal threats or even monetary payment can generally overcome any technical measures to control access. It is important to understand the attack vectors that can penetrate a known weakness in the attack surface.
It is usually highly desirable to have an independent security lab provide accreditation as to the security achieved by a particular SED or FDE technology. Recently, a number of countries and industry experts have convened and have now released Common Criteria Protection Profiles for independent labs to use for hardware SEDs and software FDE. The two profiles below are for the hardware encryption engine and the user authentication, respectively, both for hardware SEDs and software FDE:
- Common Criteria Protection Profile for FDE
- Common Criteria Protection Profile for FDE Authentication
Common Criteria certification is somewhat superior to FIPS 140-2 in that it lays out clearly what is protected against and how and so is somewhat easier to understand. However, no certification provides comprehensive security control. There are system cryptographers mainly at Universities and various cryptography houses who can also provide a relying party with the concerns that may still exist.